analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
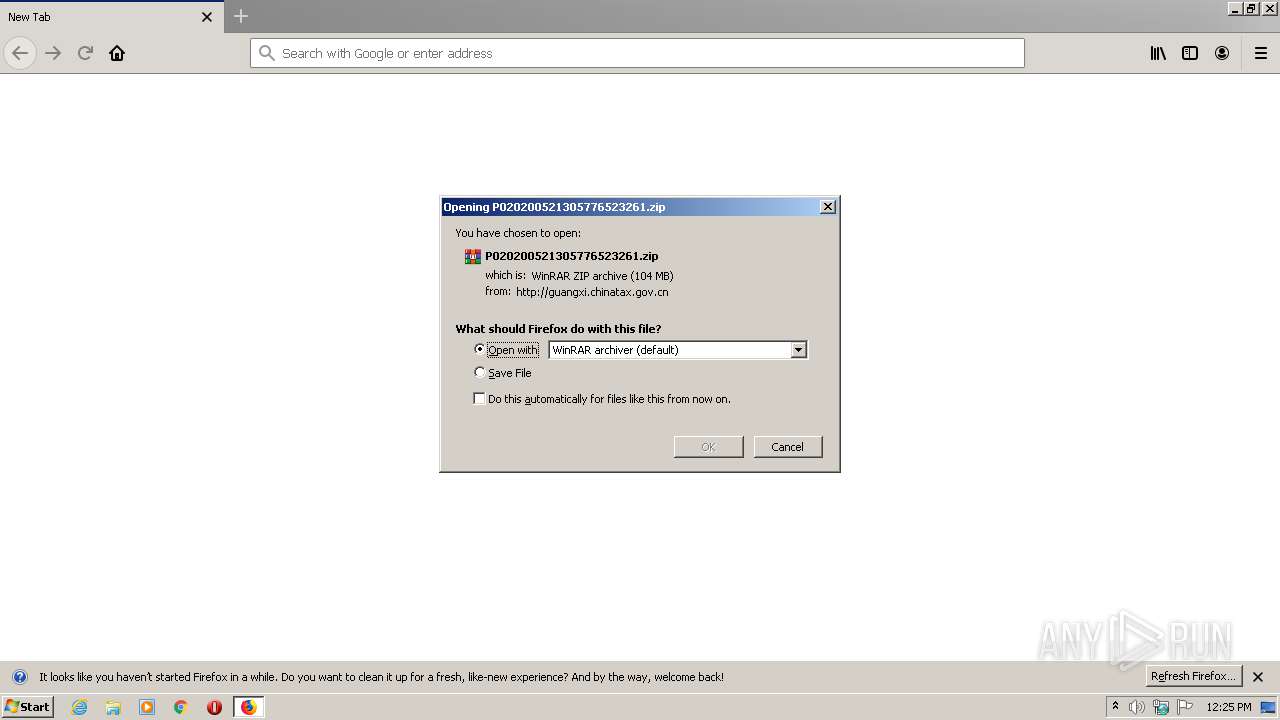
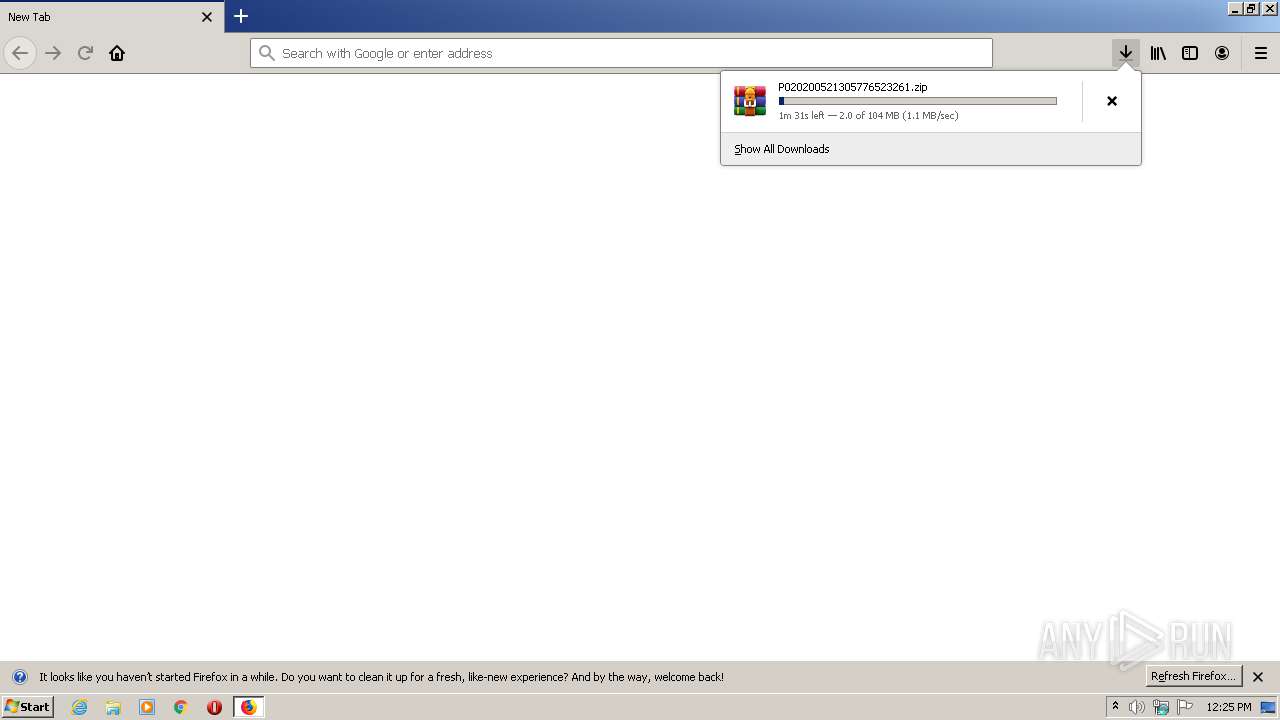
| URL: | http://guangxi.chinatax.gov.cn/nsfw/xzzx/201808/P020200521305776523261.zip |
| Full analysis: | https://app.any.run/tasks/3ada024d-479c-4f7e-ae9b-6e4076b2a939 |
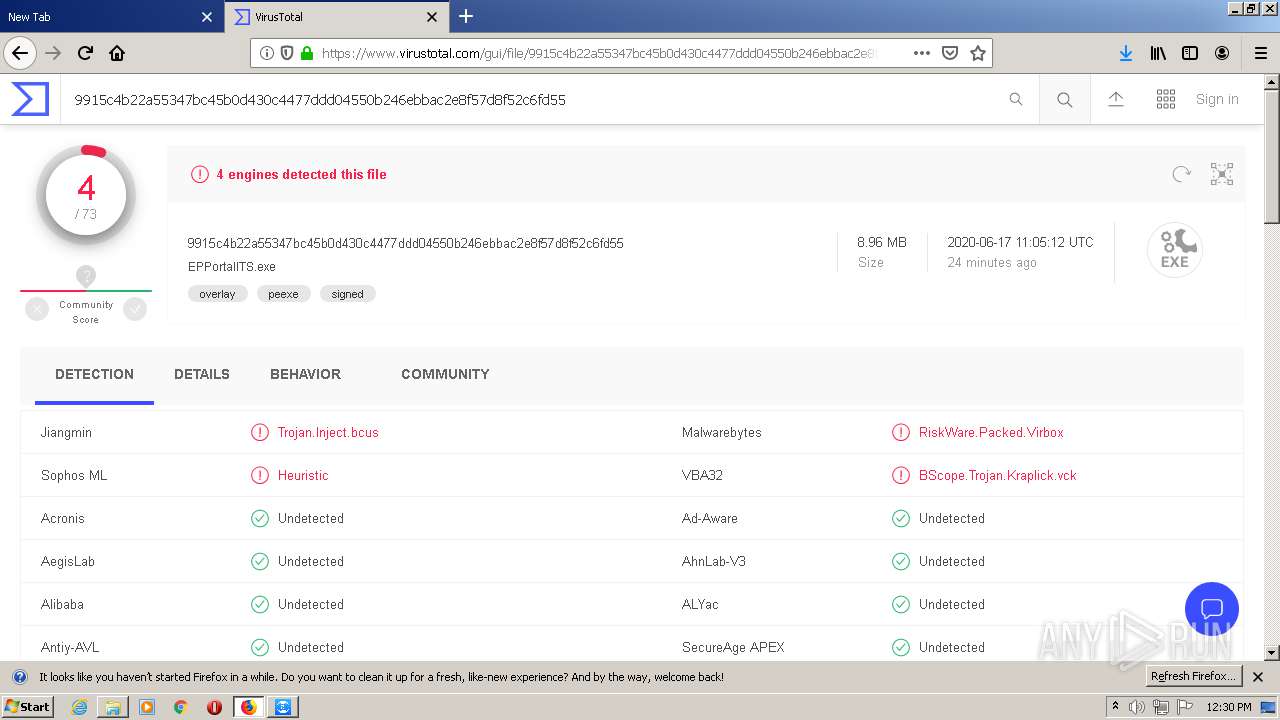
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2020, 11:25:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
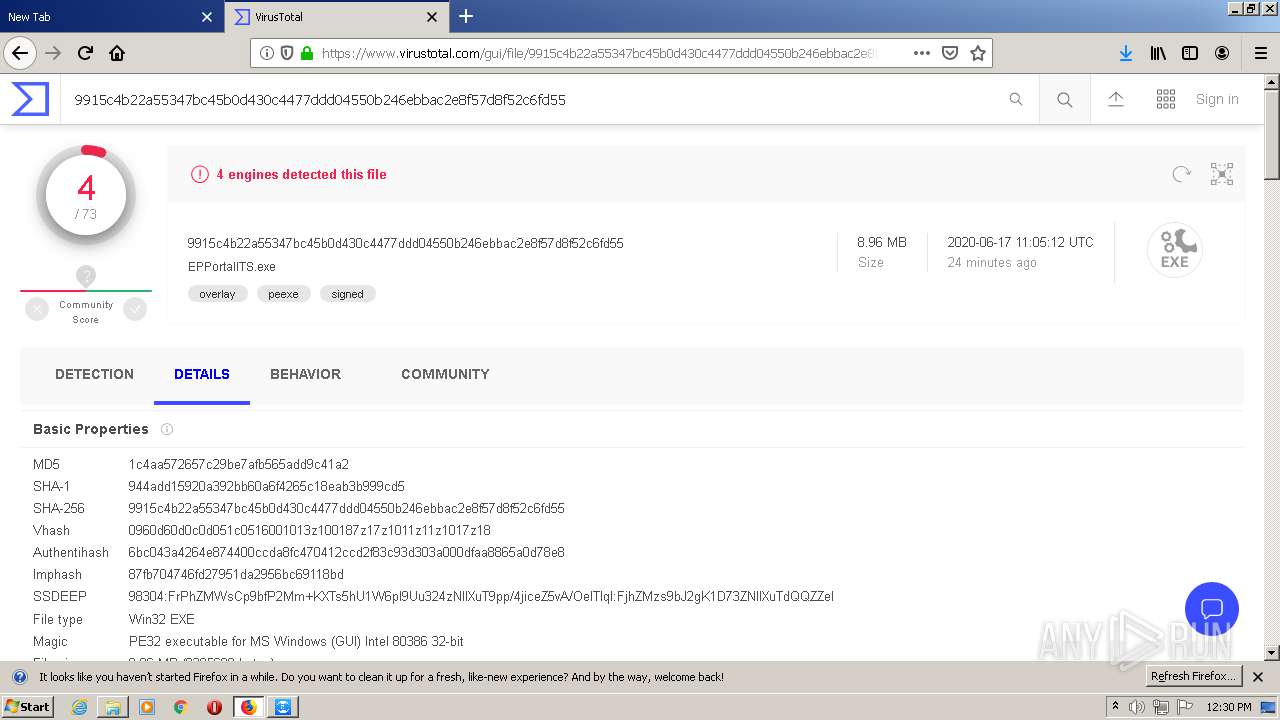
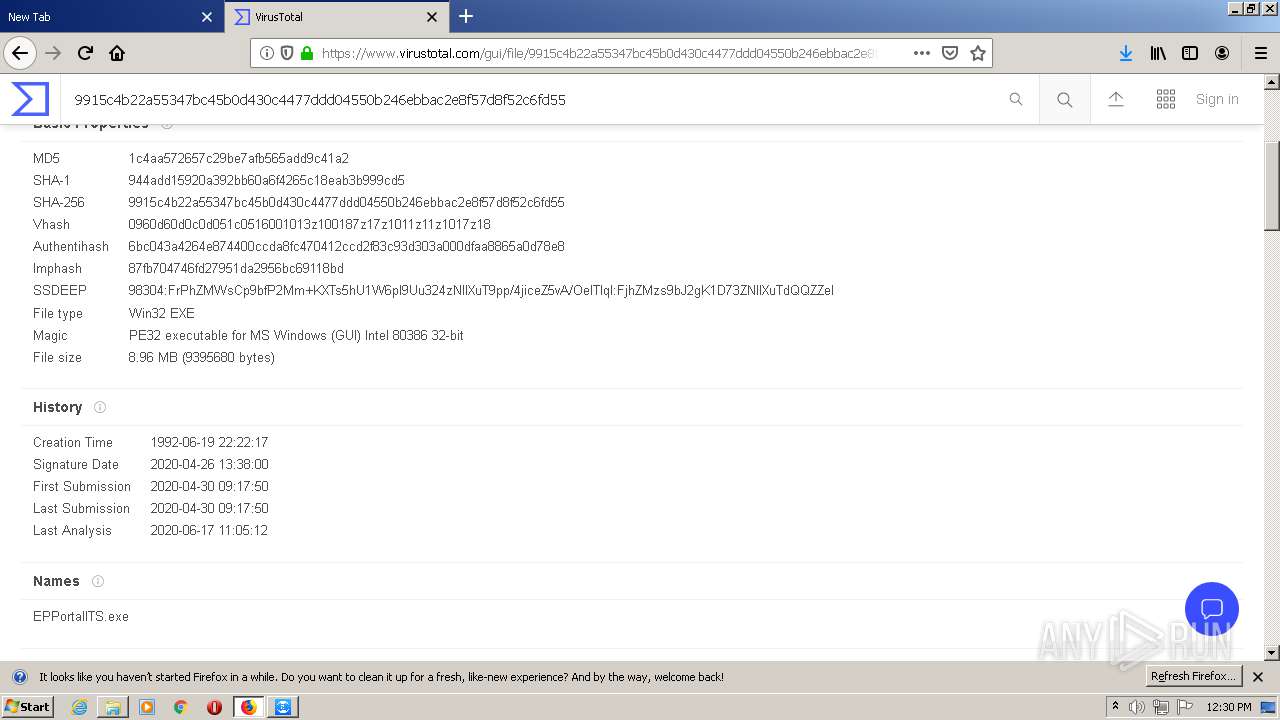
| MD5: | 9379800191CE99E8C54872279CC5A623 |
| SHA1: | 240EFD49F8FEE3CC40634C1151A28103D1A2C3E5 |
| SHA256: | AAF280A77DF37F2992A8C40302B7052B3F481611FAB81768489FAF2D690C0DA3 |
| SSDEEP: | 3:N1KZQE6MTzCKTLeuE3K1VsVQSgQXGnn:CuE60uN53KUVQSgCsn |
MALICIOUS
Application was dropped or rewritten from another process
- DaemonInstaller.exe (PID: 2632)
- ahsSetup.exe (PID: 3292)
- ssync_installer.exe (PID: 2700)
- sssync.exe (PID: 2988)
- ahs_service.exe (PID: 1916)
- ahs_service.exe (PID: 2728)
- ahs_service.exe (PID: 1308)
- EPPortalITS.exe (PID: 1888)
- EPEmergency.exe (PID: 2724)
- RepaireSqliteTools.exe (PID: 2132)
- EPPortalITS.exe (PID: 440)
- EPEmergency.exe (PID: 2352)
- RepaireSqliteTools.exe (PID: 680)
- DaemonInstaller.exe (PID: 3028)
- ProcDataDeal.exe (PID: 1916)
- ProcDataDeal.exe (PID: 3564)
- ProcDataDeal.exe (PID: 2960)
- EPPortalITS.exe (PID: 2240)
- Servyoubgup.exe (PID: 1524)
- EPPortalITS.exe (PID: 2212)
- DaemonInstaller.exe (PID: 2888)
- EPEmergency.exe (PID: 1512)
- RepaireSqliteTools.exe (PID: 3880)
- ProcDataDeal.exe (PID: 316)
- ProcDataDeal.exe (PID: 580)
- ProcDataDeal.exe (PID: 916)
- EPEnvUpdate.exe (PID: 2496)
- DMInstBoot.exe (PID: 2256)
- PTXBootSvc.exe (PID: 1780)
- EPEvenue_SH.exe (PID: 1248)
- EPEvenue_SH.exe (PID: 956)
- ITSReSetTool.exe (PID: 1716)
- ITSReSetTool.exe (PID: 1100)
- ITSReSetTool.exe (PID: 2176)
- EPEvenue_SH.exe (PID: 2716)
- SYPNS.exe (PID: 932)
Loads dropped or rewritten executable
- ahsSetup.exe (PID: 3292)
- ssync_installer.exe (PID: 2700)
- EPEvenue_SH.exe (PID: 2716)
- EPPortalITS.exe (PID: 1888)
- RepaireSqliteTools.exe (PID: 2132)
- EPEvenue_SH.exe (PID: 956)
- DMInstBoot.exe (PID: 2256)
- EPPortalITS.exe (PID: 440)
- svchost.exe (PID: 3312)
- explorer.exe (PID: 308)
- RepaireSqliteTools.exe (PID: 680)
- DaemonInstaller.exe (PID: 3028)
- DaemonInstaller.exe (PID: 2632)
- svchost.exe (PID: 2656)
- ProcDataDeal.exe (PID: 3564)
- PTXBootSvc.exe (PID: 1780)
- ProcDataDeal.exe (PID: 2960)
- Servyoubgup.exe (PID: 1524)
- ProcDataDeal.exe (PID: 1916)
- EPPortalITS.exe (PID: 2212)
- EPEvenue_SH.exe (PID: 1248)
- EPPortalITS.exe (PID: 2240)
- DaemonInstaller.exe (PID: 2888)
- RepaireSqliteTools.exe (PID: 3880)
- ProcDataDeal.exe (PID: 316)
- ProcDataDeal.exe (PID: 580)
- EPEnvUpdate.exe (PID: 2496)
- ProcDataDeal.exe (PID: 916)
Actions looks like stealing of personal data
- explorer.exe (PID: 308)
Starts NET.EXE for service management
- EPEvenue_SH.exe (PID: 2716)
- EPEvenue_SH.exe (PID: 956)
- EPEvenue_SH.exe (PID: 1248)
Changes settings of System certificates
- EPEvenue_SH.exe (PID: 2716)
- EPEmergency.exe (PID: 2724)
- DMInstBoot.exe (PID: 2256)
SUSPICIOUS
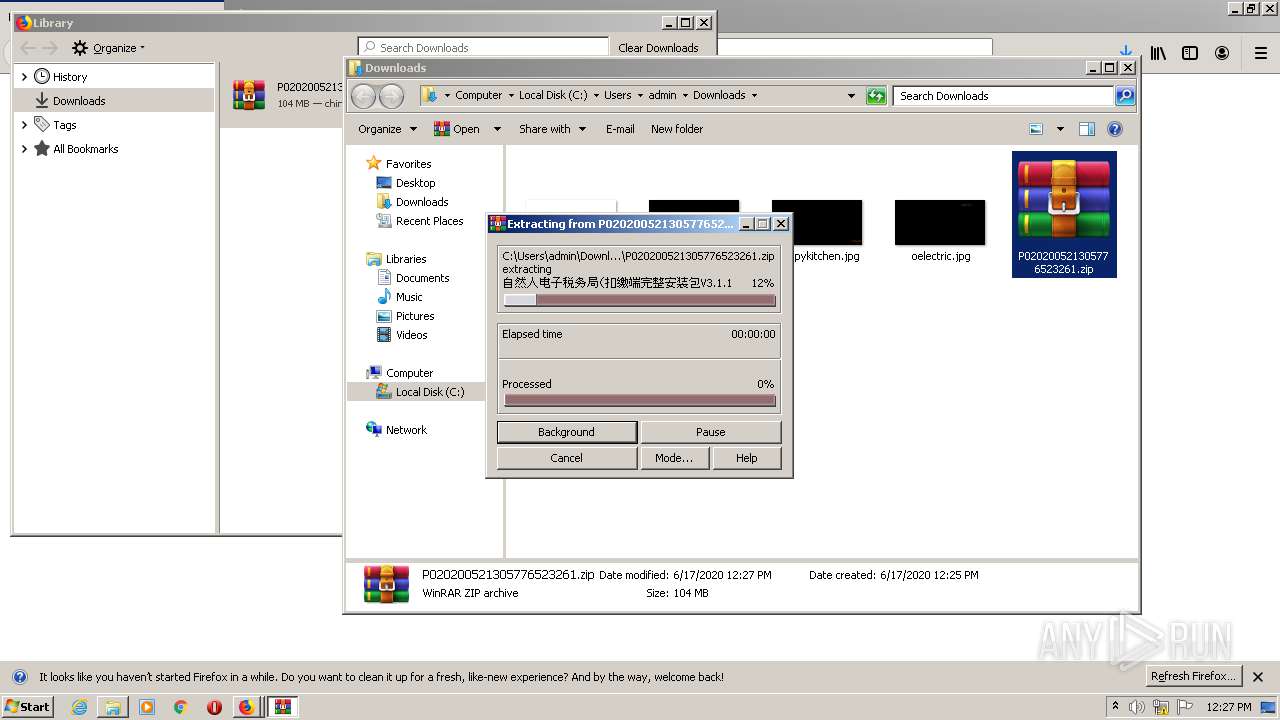
Reads Windows owner or organization settings
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
Executable content was dropped or overwritten
- 自然人电子税务局(扣缴端完整安装包V3.1.107).exe (PID: 628)
- 自然人电子税务局(扣缴端完整安装包V3.1.107).exe (PID: 2304)
- DaemonInstaller.exe (PID: 2632)
- ahsSetup.exe (PID: 3292)
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
- ssync_installer.exe (PID: 2700)
- ITSReSetTool.exe (PID: 1100)
- DaemonInstaller.exe (PID: 3028)
- Servyoubgup.exe (PID: 1524)
- DaemonInstaller.exe (PID: 2888)
Reads the Windows organization settings
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
Creates files in the program directory
- firefox.exe (PID: 3876)
- ahsSetup.exe (PID: 3292)
- sssync.exe (PID: 2988)
- ssync_installer.exe (PID: 2700)
- EPPortalITS.exe (PID: 1888)
Creates files in the user directory
- explorer.exe (PID: 308)
- DaemonInstaller.exe (PID: 2632)
- ahsSetup.exe (PID: 3292)
Starts application with an unusual extension
- ahsSetup.exe (PID: 3292)
Creates a software uninstall entry
- ahsSetup.exe (PID: 3292)
Creates or modifies windows services
- DaemonInstaller.exe (PID: 2632)
- ahsSetup.exe (PID: 3292)
- DaemonInstaller.exe (PID: 3028)
Starts SC.EXE for service management
- EPEvenue_SH.exe (PID: 2716)
Executed as Windows Service
- ahs_service.exe (PID: 2728)
Creates files in the Windows directory
- ahs_service.exe (PID: 2728)
Removes files from Windows directory
- ahs_service.exe (PID: 2728)
Creates files in the driver directory
- ahs_service.exe (PID: 2728)
Changes IE settings (feature browser emulation)
- EPPortalITS.exe (PID: 1888)
Reads Internet Cache Settings
- EPEmergency.exe (PID: 2724)
- Servyoubgup.exe (PID: 1524)
- EPEmergency.exe (PID: 1512)
Adds / modifies Windows certificates
- EPEvenue_SH.exe (PID: 2716)
- EPEmergency.exe (PID: 2724)
- DMInstBoot.exe (PID: 2256)
INFO
Loads dropped or rewritten executable
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
Application was dropped or rewritten from another process
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2572)
Manual execution by user
- WinRAR.exe (PID: 2564)
- 自然人电子税务局(扣缴端完整安装包V3.1.107).exe (PID: 2304)
Application launched itself
- firefox.exe (PID: 2168)
- firefox.exe (PID: 3876)
Reads Internet Cache Settings
- firefox.exe (PID: 3876)
Reads CPU info
- firefox.exe (PID: 3876)
Creates files in the user directory
- firefox.exe (PID: 3876)
Creates a software uninstall entry
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
Creates files in the program directory
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
Dropped object may contain Bitcoin addresses
- 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp (PID: 2844)
- ITSReSetTool.exe (PID: 1100)
Reads settings of System Certificates
- EPEvenue_SH.exe (PID: 2716)
- EPEmergency.exe (PID: 2724)
- DMInstBoot.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
115
Monitored processes
61
Malicious processes
24
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2168 | "C:\Program Files\Mozilla Firefox\firefox.exe" "http://guangxi.chinatax.gov.cn/nsfw/xzzx/201808/P020200521305776523261.zip" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 | ||||
| 3876 | "C:\Program Files\Mozilla Firefox\firefox.exe" http://guangxi.chinatax.gov.cn/nsfw/xzzx/201808/P020200521305776523261.zip | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 68.0.1 | ||||
| 2004 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3876.0.209442294\1577203504" -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3876 "\\.\pipe\gecko-crash-server-pipe.3876" 1184 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 68.0.1 | ||||
| 3912 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3876.3.1648214197\1578259056" -childID 1 -isForBrowser -prefsHandle 808 -prefMapHandle 1640 -prefsLen 1 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3876 "\\.\pipe\gecko-crash-server-pipe.3876" 1068 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 68.0.1 | ||||
| 3972 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3876.13.857138288\373918432" -childID 2 -isForBrowser -prefsHandle 2916 -prefMapHandle 2920 -prefsLen 5996 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3876 "\\.\pipe\gecko-crash-server-pipe.3876" 2936 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 68.0.1 | ||||
| 2640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3876.20.412508244\689506273" -childID 3 -isForBrowser -prefsHandle 3772 -prefMapHandle 3768 -prefsLen 6718 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3876 "\\.\pipe\gecko-crash-server-pipe.3876" 3752 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 68.0.1 | ||||
| 2564 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\P020200521305776523261.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 2304 | "C:\Users\admin\Downloads\自然人电子税务局(扣缴端完整安装包V3.1.107).exe" | C:\Users\admin\Downloads\自然人电子税务局(扣缴端完整安装包V3.1.107).exe | explorer.exe | |
User: admin Company: 税友软件集团股份有限公司 Integrity Level: MEDIUM Description: 自然人电子税务局(扣缴端) Setup Exit code: 0 Version: | ||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\is-DC3Q4.tmp\自然人电子税务局(扣缴端完整安装包V3.1.107).tmp" /SL5="$301E0,108416035,184320,C:\Users\admin\Downloads\自然人电子税务局(扣缴端完整安装包V3.1.107).exe" | C:\Users\admin\AppData\Local\Temp\is-DC3Q4.tmp\自然人电子税务局(扣缴端完整安装包V3.1.107).tmp | — | 自然人电子税务局(扣缴端完整安装包V3.1.107).exe |
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 | ||||
| 628 | "C:\Users\admin\Downloads\自然人电子税务局(扣缴端完整安装包V3.1.107).exe" /SPAWNWND=$20224 /NOTIFYWND=$301E0 | C:\Users\admin\Downloads\自然人电子税务局(扣缴端完整安装包V3.1.107).exe | 自然人电子税务局(扣缴端完整安装包V3.1.107).tmp | |
User: admin Company: 税友软件集团股份有限公司 Integrity Level: HIGH Description: 自然人电子税务局(扣缴端) Setup Exit code: 0 Version: | ||||
Total events
8 508
Read events
6 217
Write events
0
Delete events
0
Modification events
Executable files
307
Suspicious files
886
Text files
1 738
Unknown types
106
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3876 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:DE9496ACA551ADE408EF6466A11833A1 | SHA256:8F9C7FDB3E0BC01024E43A8E242468FC4DD4F74C725E32A883571635203DC10A | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:354459382F30B8994109C88659DFA1F3 | SHA256:E3E8E2B7E7EECA231620D83C70FA5A926E8B9CE74C51F595F71191DC0B50527E | |||
| 3876 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:5027177F513CDAE07DB2330E1DED5934 | SHA256:0C53F16051E738287A4612F68E296238087627E594CFD6DDFA1FECC2E998328B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
68
DNS requests
136
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2496 | EPEnvUpdate.exe | POST | — | 218.75.34.94:7002 | http://hawk.servyou.com.cn:7002/hawk/subjectgate.htm | CN | — | — | unknown |
1524 | Servyoubgup.exe | GET | 200 | 47.246.43.225:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | US | der | 471 b | whitelisted |
2724 | EPEmergency.exe | GET | 200 | 93.184.220.29:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR3enuod9bxDxzpICGW%2B2sabjf17QQUkFj%2FsJx1qFFUd7Ht8qNDFjiebMUCEANOP%2Fk75lbZcs%2Bm2RM%2F5ys%3D | US | der | 471 b | whitelisted |
3876 | firefox.exe | POST | 200 | 216.58.205.227:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
3876 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
3876 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3876 | firefox.exe | GET | 200 | 222.216.1.203:80 | http://guangxi.chinatax.gov.cn/nsfw/xzzx/201808/P020200521305776523261.zip | CN | compressed | 104 Mb | unknown |
3876 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3876 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
3876 | firefox.exe | POST | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1o1core | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3876 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3876 | firefox.exe | 52.41.191.52:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3876 | firefox.exe | 143.204.202.50:443 | snippets.cdn.mozilla.net | — | US | malicious |
3876 | firefox.exe | 216.58.205.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3876 | firefox.exe | 2.16.186.50:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3876 | firefox.exe | 172.217.23.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3876 | firefox.exe | 143.204.202.9:443 | firefox.settings.services.mozilla.com | — | US | malicious |
3876 | firefox.exe | 222.216.1.203:80 | guangxi.chinatax.gov.cn | No.31,Jin-rong Street | CN | unknown |
3876 | firefox.exe | 2.16.186.17:443 | shavar.services.mozilla.com | Akamai International B.V. | — | whitelisted |
3876 | firefox.exe | 34.210.182.212:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
guangxi.chinatax.gov.cn |
| unknown |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
d228z91au11ukj.cloudfront.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
Process | Message |
|---|---|
svchost.exe | [FindSYKeeperConfigRegs]Access violation at address 003B043A in module 'SYbgupKeeper.dll'. Read of address 00000008 |
svchost.exe | CreateProcessAsCurrentUser_Vista success. |
svchost.exe | CreateProcessAsCurrentUser_Vista success. |
svchost.exe | CreateProcessAsCurrentUser_Vista success. |
EPEvenue_SH.exe | [EPEvenue_SH.exe][xppngimage]:Register TPNGObject |
sssync.exe | [DSS_CLIENT]490> [dss_cli_send_async] send_len = 244 error_code = 0x40000000 |
EPPortalITS.exe | [XPFarmer.bpl][xppngimage]:Register TPNGObject |
EPPortalITS.exe | + [524]Ö÷Ï̱߳» ´´½¨ |
EPPortalITS.exe | + [TAnimationSplashForm:1872]Ïß³Ì[Suspended:True]±» ´´½¨ |
EPPortalITS.exe | + [TAsyncCallThread:2820]Ïß³Ì[Suspended:False]±» ´´½¨ |